Creating a Fortress of Protection with an Integrated Security Solution
Integrated security solutions offer a comprehensive and holistic approach to safeguarding your environment and work in harmony to create a seamless defense against potential threats.

Real-Time Monitoring and Incident Response Reduces Complexity
Integration allows for real-time monitoring of all security components from a centralized location. Security personnel can quickly identify and respond to incidents, reducing response times and mitigating threats. It also simplifies system training and the user experience.
Scalable and Adaptable
Scale an integrated solution to accommodate growth or configuration changes to meet new requirements. This adaptability ensures the security solution remains effective as your environment changes.
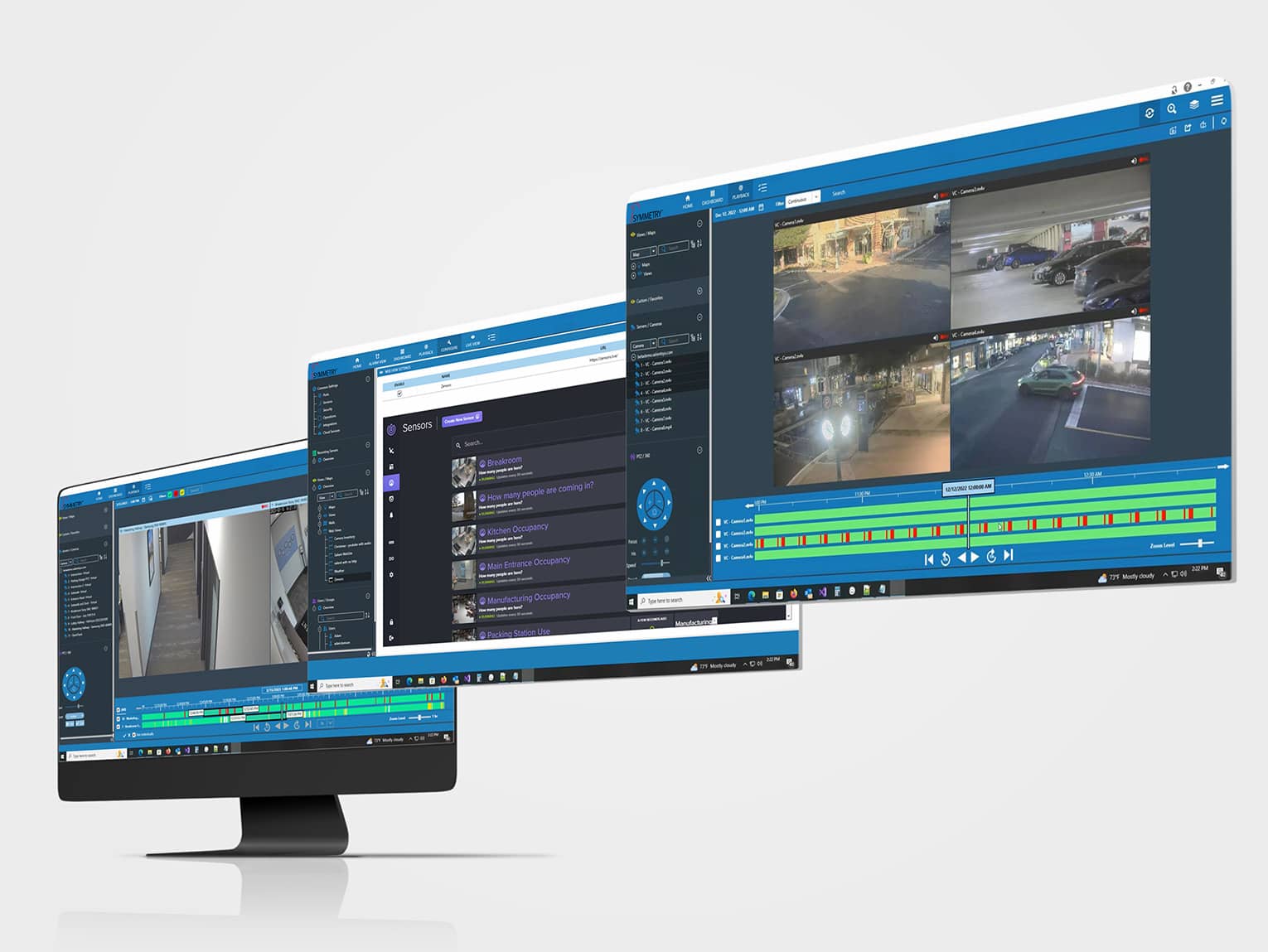
Streamline Operations
Manage access control, video management and other systems from a single platform, reducing the complexity of managing multiple systems. Managing Symmetry systems and third-party technologies on a single platform reduces costs and improves efficiency.
Cost
Efficient
Cost Efficient
Combining multiple security systems into one not only reduces installation and maintenance costs but also minimizes false alarms and costly downtime.
Data Analysis
and Reporting
Data Analysis and Reporting
Integrated solutions provide a wealth of data that can be analyzed to improve security measures. Detailed reports on access patterns, security incidents and system performance enable better decision-making, ultimately enhancing security measures and reducing risks.
Compliance
Requirements
Compliance Requirements
Installing an integrated solution makes it easier to meet compliance standards in highly regulated industries such as data centers, utilities and finance. You can manage access control policies, track security incidents and produce audit reports more effectively.
Ready to get started?
Learn how the Symmetry™ Security Management System and its ~120 technology integrations can effectively secure your organization.
