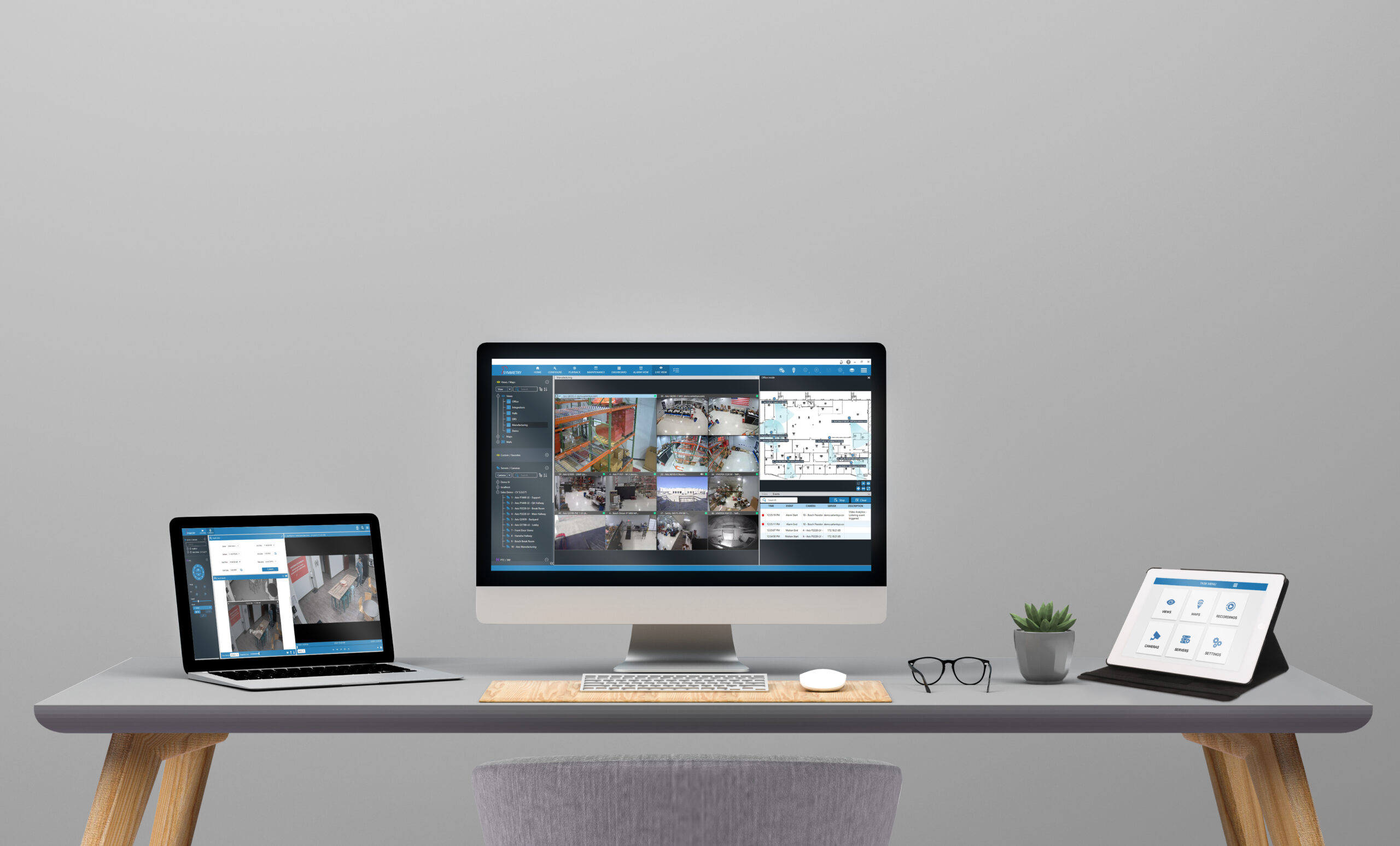
End-user needs are changing because the dynamics of how organizations function are changing. Companies are forced to use the cost down approach and do more with less. What does that mean? Companies must look at the big picture and determine how to mitigate risk, ensure compliance and reduce costs in the most efficient way possible. How can a manufacturer help an organization become more efficient while they adopt a low cost of deployment and ownership mentality?
Look at the Big Picture and Drill Down
Security touches everyone in the company, so we recommend conducting an organizational workshop and inviting department heads from every department. You’ll be surprised at the discussions, and the outside departments will come to value the security department’s contribution to the company. Because as I’ve seen, security is often viewed as a necessary evil in an organization. A workshop can change that.
We approach the workshop in a methodical way that uncovers key components to understanding how to build a successful program that includes buy-in from other departments.
Starting at the beginning, we ask lots of questions that help us understand the company. For example, what types of identities are allowed in a facility? Who decides what level of access an identity receives? How many levels of access are there and how does an identity qualify to obtain a certain level? You must understand what is important to an organization so you can offer a solution to their challenges. The solution must provide value to each stakeholder. So you ask a lot of questions, such as why does a door need to be locked down? Is something sensitive behind the door? Is there a compliance reason? You must understand how they work as an organization…you must understand their risk.
We review what technologies are used to secure the premises. Are they effective? What is missing? How do the technologies touch the different departments? What input does the head of HR have about the access control system? Would the legal department add or change a technology to become more efficient and keep the company in compliance? If budget wasn’t an issue, what technologies would you add or change?
Next, we review the processes used with those technologies. What happens when an alarm comes in? What is the process used to address each and every alarm? Is it working? Would the company improve its operational efficiency if better workflows were implemented?
As discussions unfold, the outside departments will see how security affects their part of the business. HR will understand they can use camera footage to review slip and falls. Or the marketing team will see how store traffic patterns could affect where product is placed. Legal department’s are concerned about compliance and an identity management system could help take a proactive approach. Everyone is concerned about violent situations. Could a visitor management system help prevent one?
The workshop reveals strengths and weaknesses in a security program, and prompts discussion about the solutions needed to be more effective and efficient. From this, the security team, with the support of all departments, can create a business case and plan moving forward. Now that there is buy in from the other departments, they may kick in part of their budget to help make the new plan a reality. Everyone benefits.
There is a big emphasis in the market to upgrade to more secure technology. As enterprise customers are doing more with less, they must choose products and solutions that support existing technology while upgrading. Upgrading to Bluetooth readers provides a future-proof solution.
A large part of the market still uses unsecure Wiegand technology. AMAG’s multi-technology transition reader, Symmetry Blue, allows the customer to use their existing credentials today until they completely transition to a more secure credential. Our reader supports Wiegand technology, but then allows the customer to later update the firmware to support the more secure OSDP communications protocol. Customers can always use the existing cabling as they upgrade, supporting least cost of deployment and ownership.
ID issuance has created operational burdens on organizations with hundreds or thousands of employees. First, the cost of the ID itself is expensive, and second, the management of the ID is cumbersome and expensive. Old employee’s pictures are not updated, creating a security risk. Physically taking pictures of old employees and replacing the physical badges is a massive company initiative and expense.
Organizations are now moving to digital IDs and a mobile solution for access control. Building out the digital credential is free and moving it to a digital device via an app that pushes information back to the Symmetry system is fast, easy and inexpensive. This can be done remotely. Moving to a mobile solution supports least cost of ownership and deployment and drives efficiencies.
With end users operating on tighter budgets and under pressure to upgrade to more secure technology, a free organizational workshop identifies needs and provides a roadmap to meet company goals. Is this something your organization would consider?

By AMAG Technology, Sr. Director of Global Sales, Justin Wilmas